Last changed: 11.07.2019
Basic binary analysis
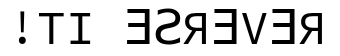
echo c68e c6a7 d0af c68e 56 c68e d0af | xxd -ps -rhashsum checks
To check if a binary gets recognized as malware or if it is already known you query virustotal.com for the file or its hash.
md5sum <file>
sha1sum <file>
pehash <file>To search for similar files you could use the fuzzy ssdeep hash or the imphash
which hashes only the import address table of binaries.
virustotal.com offers the search modifiers
ssdeep:"<HASH> <SCORE>" and imphash:<HASH>.
ssdeep <file>imphash.py
import pefile
pe = pefile.PE('evil.exe')
pe.get_imphash()compare binary files
cmp -l <file1> <file2> | gawk '{printf "%08X %02X %02X\n", $1-1, strtonum(0$2), strtonum(0$3)}'
vbindiff <file1> <file2>PE information (linux)
For some basic static analysis of a PE file linux offers some command line tools.
basic identification
file <file>string search
strings <file>
strings -el <wide-char-file>
pestr <file>show headers, sections, import & exports
readpe -h coff <file>
readpe -S <file>
readpe -i -e <file>To resolve imports by ordinals you can use objdump or radare2. At this moment it seems as if radare2 does ignore the ordinal offset.
objdump -p <my_dll>
r2 -qc iE <my_dll> | grep ord=003 | cut -d " " -f 3,8scan for suspicious artifacts
peframe <file>disassemble selected instructions
pedis -e -i 10 <file>
pedis -s .text <file>identify packer
pepack -d userdb.txt <file>show security features
pesec <file>extract ressources
for f in *exe; do echo "$f"; peres -s "$f"; done
peres -l <file>
peres -X <file>The listing and the named extraction were patched into peres in June 2018. So I
make sure to use a recent version from the
git repository.
ELF information (linux)
show headers, sections, symbols
readelf -h <file>
readelf -S <file>
readelf --dyn-syms <file>show dynamically linked libraries
ldd <file>disassemble selected instructions
objdump -dMintel <file> | grep \<main -A 30PE information (windows)
PEiD(identify packer)PEview(show header)dependency walker(show imports/exports)PEStudio(scans for suspicious artifacts)
basic dynamic analysis (windows)
To run dynamic analysis of a PE file you could monitor its execution in a safe windows environment. To simulate an internet connection I use inetsim on another linux machine.
echo -n "Microsoft NCSI" > /var/lib/inetsim/http/fakefiles/sample.txtFor Windows 10 it should be
echo -n "Microsoft Connect Test" > /var/lib/inetsim/http/fakefiles/sample.txtexecute exported dll function
rundll32.exe <my_dll>,<function> [<parameter>]This can be used to start the function in a debugger like x64dbg. Then you
could create a dll breakpoint to stop when the dll is loaded.
service dlls
A function called ServiceMain can indicate, that the dll shall run as a
service. Sometime a function to install the service is also present.
The function can be executed through rundll32.exe. The name of the new service
can be found with regshot or procmon.exe.
sc qc <my_service>
net start <my_service>procexp.exe (SysinternalsSuite)
Some very useful functions of the procexp.exe are
- list process tree and see orphaned processes
- compare strings of image and of process memory
- find processes by dll name
- list dlls, handles and mutexes
- verify signed binaries
- suspend or kill processes
procmon.exe (SysinternalsSuite)
procmon.exe can be used to capture and filter events. To quickly find system
modifications or process execution the following filters are useful.
ProcessName is my_process.exe
Operation is WriteFile
Operation is RegSetValue
Operation is Process CreateTo gain a quick overview procmon.exe offers a Process Tree (Ctrl+T) or
activity summaries in its Tools menue.
ProcDOT
ProcDOT can import .csv files from procmon.exe and generate a graph with
the main activity of a specified process. Furthermore this graph can be replayed
sequentially according to the timestamps recorded by procmon.exe.
regshot
To quickly see changes in the registry regshot can be used to create and compare snapshots of all registry values before and after the execution of the program.
basic dynamic analysis (linux)
To gain a first impression what a binary does you can monitor its system calls and library calls in a safe environment.
strace
Running a program through strace will print all occuring system calls, their
parameters and the return values. The output can be filtered and written to a
text file.
strace -n 100 -fi <file>
strace -e trace=open,close,write -o output.txt <file>
strace -p <pid>ltrace
When analysing a dynamically linked binary with ltrace all library calls get
printed. System calls can get included in the output.
ltrace -S -f -i <file>
ltrace -l libc.so.6 -s 100 -o output.txt <file>lsof
The program lsof helps finding opened files, pipes and network connections. It
can combine filters with OR or AND.
lsof <file> +D <directory>
lsof -u <user> -c <command> -a
lsof -i4 -p <pid>unpacking packed binaries with x64dbg
dump with scylla
- Check if OEP is correct
- Dump (-> creates new file)
fix IAT with scylla
- IAT Autosearch
- Get Imports
- Fix Dump (choose new file)
Signatures
Host and network based Indicators of Compromise can be turned into signatures to detect infected machines or malicious network traffic.
snort_example.rule
alert tcp any any -> any any (msg:"Snort example"; content:"|0d 0a|value\: evil|0d 0a|"; sid:12345; rev:1;)test snort rules
To test these rules the config has to be modified to include the rule file.
Afterwards snort can be run. If it runs on the same machine as the
communication participant checksum filtering should be disabled.
snort -i eth0 -c /etc/snort/snort.conf -A console -k noneyara_example.rule
rule yara_example {
meta:
quality = "high"
description = "evil string in pe file"
strings:
$s1 = "evil"
$s2 = "evil" wide
condition:
(1 of them) and (pe.characteristics & pe.EXECUTABLE_IMAGE)
}test yara rules
yara -rwm yara_examle.rule <folder>virustotal yara module
Virustotal offers its own yara module for live hunting.